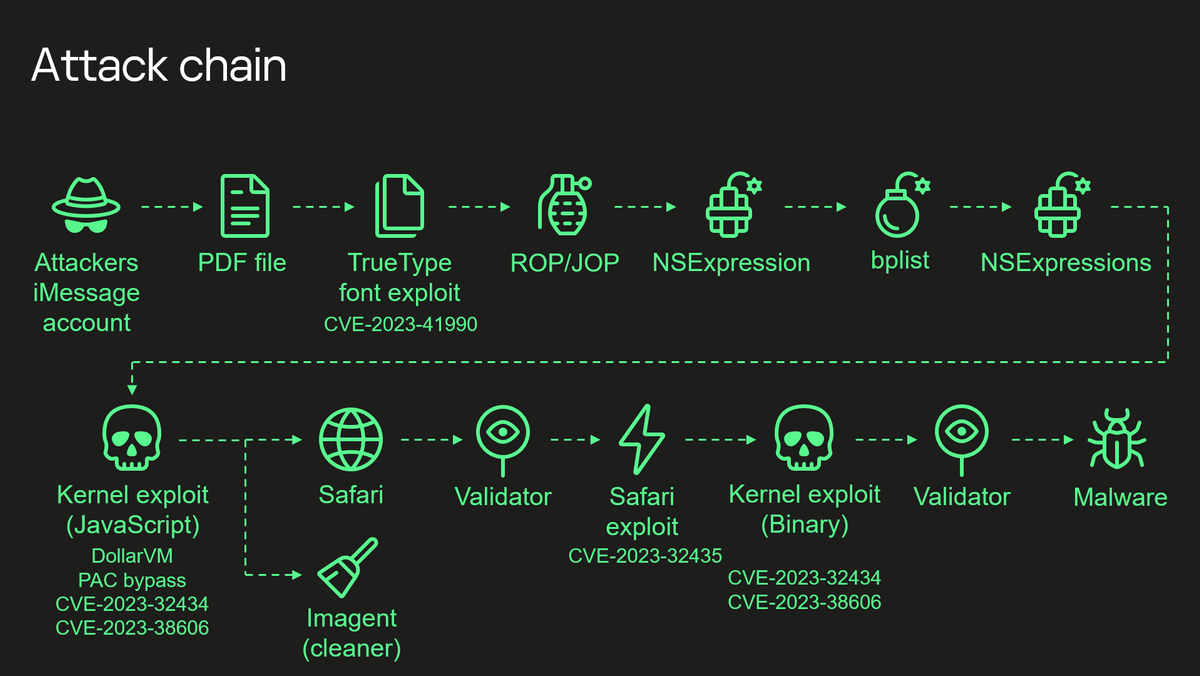
On Wednesday, security researchers from Kaspersky Lab were able to provide details of a secret cyber operation they called “operation triangulation.” Those behind the operation managed to take complete control of both new and older iPhone models using a highly advanced attack chain that exploited a total of four vulnerabilities, one of which was hardware-based.
During the fall, Apple removed or reduced the chances of exploitation of all four vulnerabilities, not only in the iPhone iOS operating system, but also in other Apple operating systems. However, one of the weak points (CVE-2023-41990) are present in the TrueType font instructions, which are said to have been present in Apple's operating systems since the early 1990s.
Bypass hardware-based protection
There is still another vulnerability that is getting the most attention In the presentation of security researchers And, among other things Ars Technicawho were early in discussing the results.
This loophole (CVE-2023-32434) makes it possible to bypass a hardware-based function that protects certain areas of kernel memory, a protection that only exists in Apple's own system chips. This made it possible to change some sensitive kernel states in the system.
Bypassing the protection function should be possible because the chips contain undocumented hardware registers that are not used by the hardware firmware. Security researchers believe the logs were either added to the chips by mistake or are intended for internal testing or debugging at Apple.
Full root access
This, combined with other vulnerabilities, allowed attackers to gain full access to the system by sending a specially crafted PDF file to the victim as an iMessage attachment. According to security researchers, this file was processed by the IMessage application without users noticing.
But as the illustration at the top of the case shows, there are many links in the attack chain that must be executed starting with the PDF file that is received for attackers to gain the desired access.
The presentation was presented to security researchers During the 37th Chaos Communications Conference In Hamburg. Ars Technica, which was in contact with security researchers, wrote that the attacks have been going on for four years. It is not known specifically who was the target of the attacks, who was behind them, how many attacks were carried out, and what was achieved. However, given the characteristics of the attack chain, the probability of success of many attacks is high.
Important experience
This is not an ordinary vulnerability, said one of the Russian security researchers, Boris Larin, during a press conference on Wednesday, according to Ars Technica.
– Due to the closed nature of the iOS ecosystem, the discovery process was difficult and time-consuming. It required a broad understanding of both hardware and software architectures. “What this discovery tells us again is that even advanced hardware-based protections can be rendered ineffective in the face of a sophisticated attacker, especially when there are hardware functions that make it possible to bypass these protections,” Larrain continued.
All vulnerabilities that were used in the “triangulation process” have thus been removed from newer Apple devices. Older devices that no longer receive security updates may still be vulnerable to similar attacks.
Security researchers have not yet finished analyzing the entire series of attacks, but they promise to return in 2024 with a detailed description of each vulnerabilities and how to exploit them.

“Web specialist. Lifelong zombie maven. Coffee ninja. Hipster-friendly analyst.”